Wallarm Connector for Amazon API Gateway (API Discovery)  ¶
¶
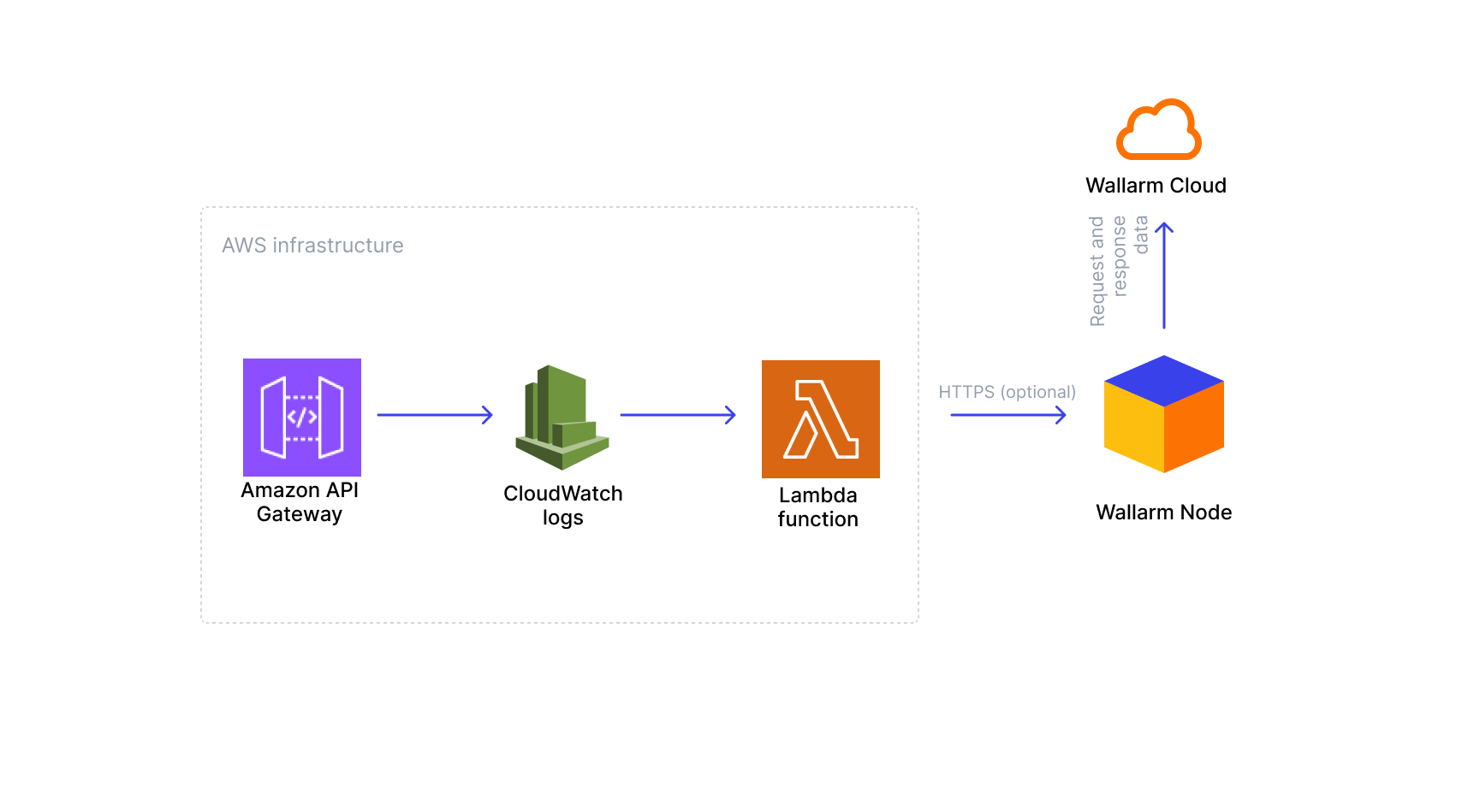
The Wallarm Connector for Amazon API Gateway automatically builds an API inventory from real traffic by relying on CloudWatch logs.
How it works¶
This connector does not inspect or block malicious requests. Instead, it uses a Lambda function to monitor CloudWatch logs from API Gateway, parse the log data, and forward relevant metadata to a Wallarm Native Node. The result is your API inventory.
The solution consists of three AWS components (your API in API Gateway, CloudWatch Logs, and a Lambda function) and one Wallarm component (Native Node), which are connected in the following way:
-
API Gateway receives requests from clients and generates CloudWatch logs for each API call.
-
CloudWatch logs capture information about each request and make it available for processing.
-
A Lambda function subscribes to these logs, reads new entries, and extracts API metadata.
-
The Lambda function forwards the extracted metadata to the Wallarm Native Node.
-
The Native Node collects this metadata and build an API inventory.
Limitations¶
At the moment, this connector does not detect or monitor attacks. Its primary purpose is to build your API inventory using the API Discovery feature.
Requirements¶
To proceed with the deployment, ensure that the following requirements are met:
-
API managed by Amazon API Gateway
-
Understanding of Amazon CloudWatch, Amazon API Gateway, and AWS Lambda technologies
-
An Advanced API Security subscription that enables the API Discovery feature
Deployment¶
1. Deploy a Wallarm node¶
The Wallarm node is a core component of the Wallarm platform that you need to deploy. It inspects incoming traffic, detects malicious activities, and can be configured to mitigate threats.
You can deploy it either hosted by Wallarm or in your own infrastructure, depending on the level of control you require.
To deploy a Wallarm-hosted node for the connector, follow the instructions.
Choose an artifact for a self-hosted node deployment and follow the attached instructions:
- All-in-one installer for Linux infrastructures on bare metal or VMs
- Docker image for environments that use containerized deployments
- Helm chart for infrastructures utilizing Kubernetes
2. Create an IAM role with an IAM policy for Lambda¶
-
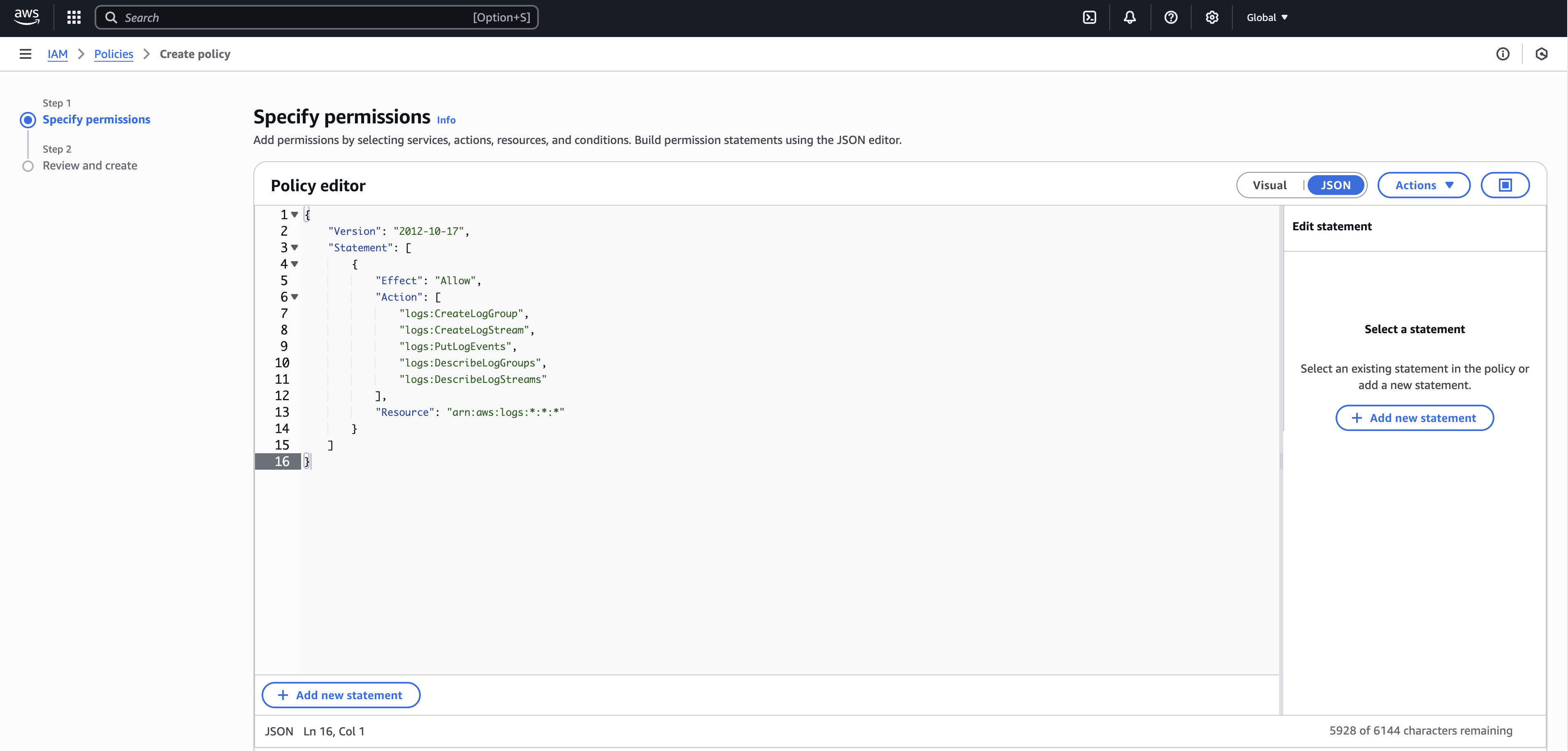
Sign in to the AWS Management Console and go to Identity and Access Management (IAM).
-
Create the following IAM policy using the JSON editor:
-
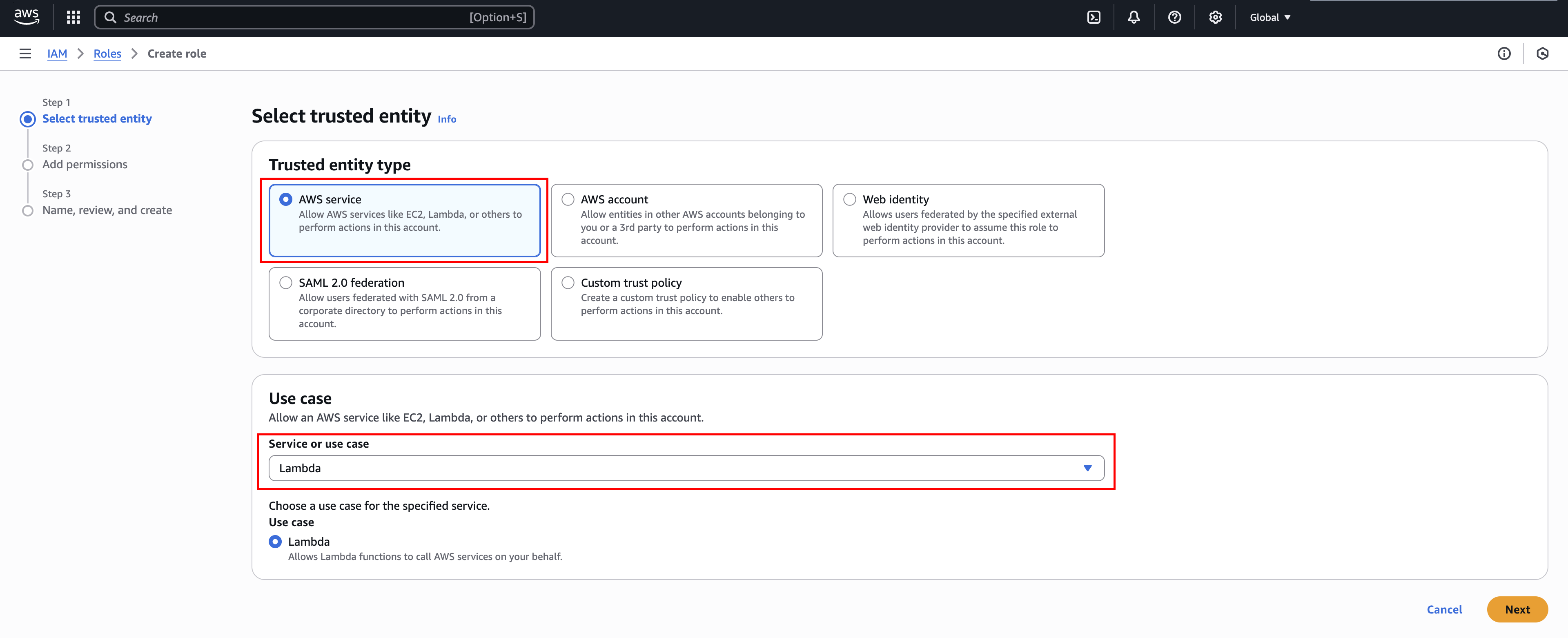
Go to Roles and click Create role.
-
Select AWS service and Lambda for "Trusted entity type" and "Use case", respectively, and then click Next.
-
On the "Add permissions" step, select the IAM policy you have created earlier, and click Next.
-
Give your IAM role a recognizable name (e.g.,
WallarmAPIDiscoveryLambdaRole) and optionally edit the role's description. -
Click Create role.
You have created the IAM role and attached the IAM policy required by the Lambda function.
See more details on creating roles and attaching policies.
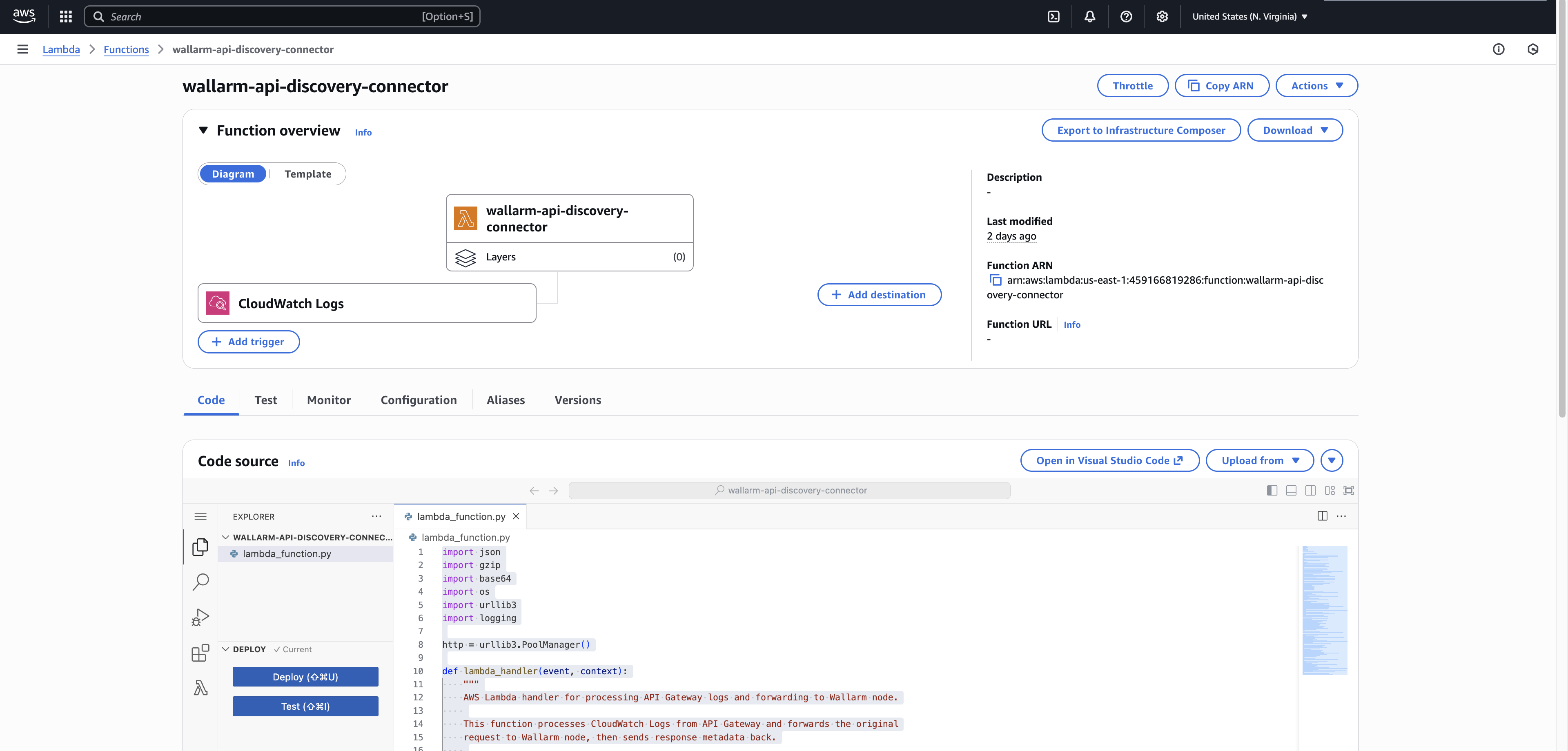
3. Create a Lambda function¶
-
Open the Functions page of the Lambda console and click Create function.
-
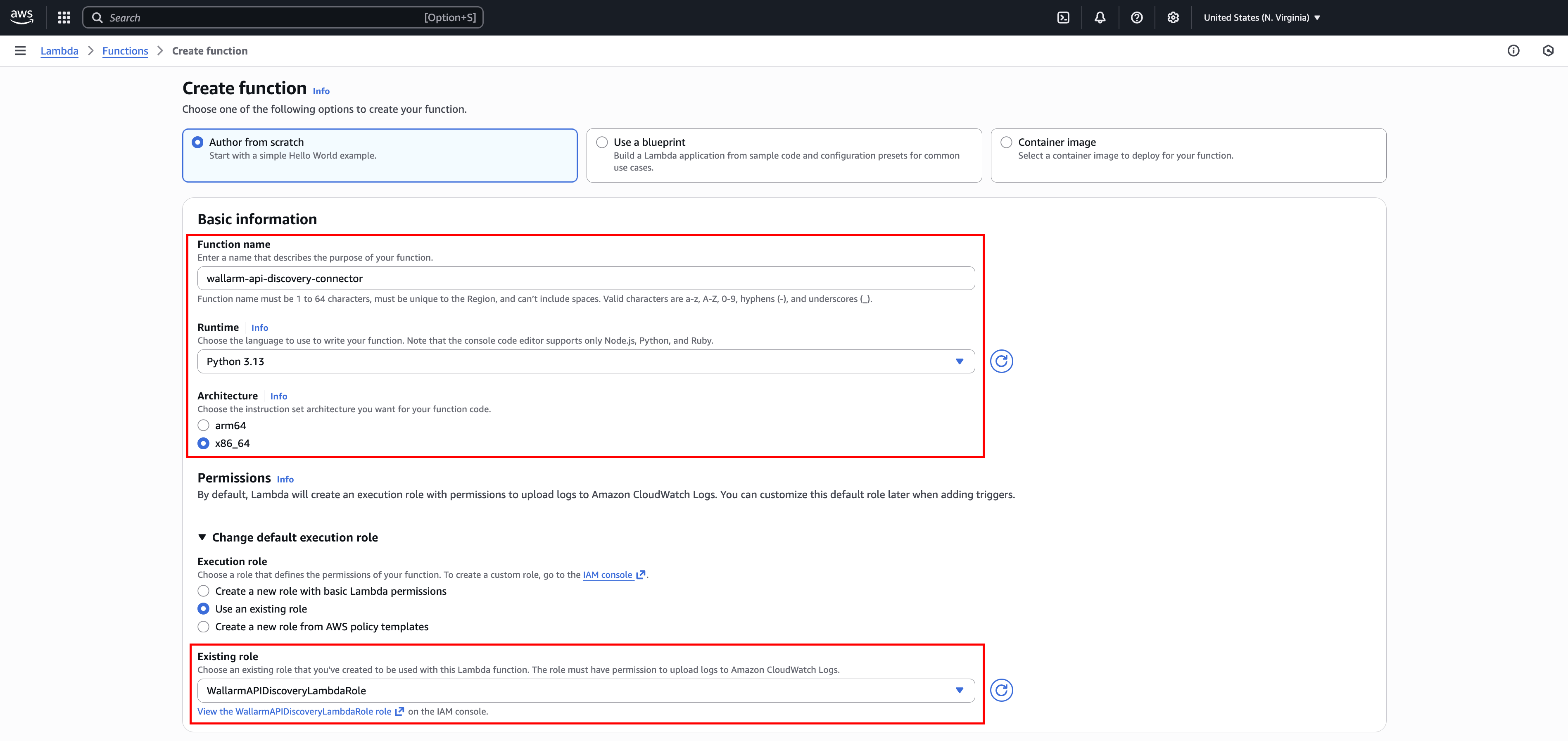
Select Author from scratch.
-
Give your function a recognizable name (e.g.,
wallarm-api-discovery-connector). -
Choose Python 3.13 and x86_64 under "Runtime" and "Architecture", respectively.
-
Under "Permissions", expand Change default execution role, select Use an existing role, and then select the IAM role you created in Step 2 (
WallarmAPIDiscoveryLambdaRole) -
Click Create function.
You have created a Lambda function. You now need to configure it to process CloudWatch logs and forward API metadata to the Wallarm node.
4. Configure the Lambda function¶
-
To configure the Lambda function, you need the Wallarm code bundle. Go to Wallarm Console → Security Edge → Connectors → Download code bundle and download the code bundle for your platform.
If you are running a self-hosted node, contact sales@wallarm.com to get the code bundle.
-
Contact sales@wallarm.com to get the Lambda function configuration for the connector.
-
Extract the code bundle archive, open the
cw-resend-lambda/lambda_function.pyfile, and copy its contents. -
In your Lambda function, go to the Code tab and paste the copied code into the "Code source" section.
-
Click Deploy.
-
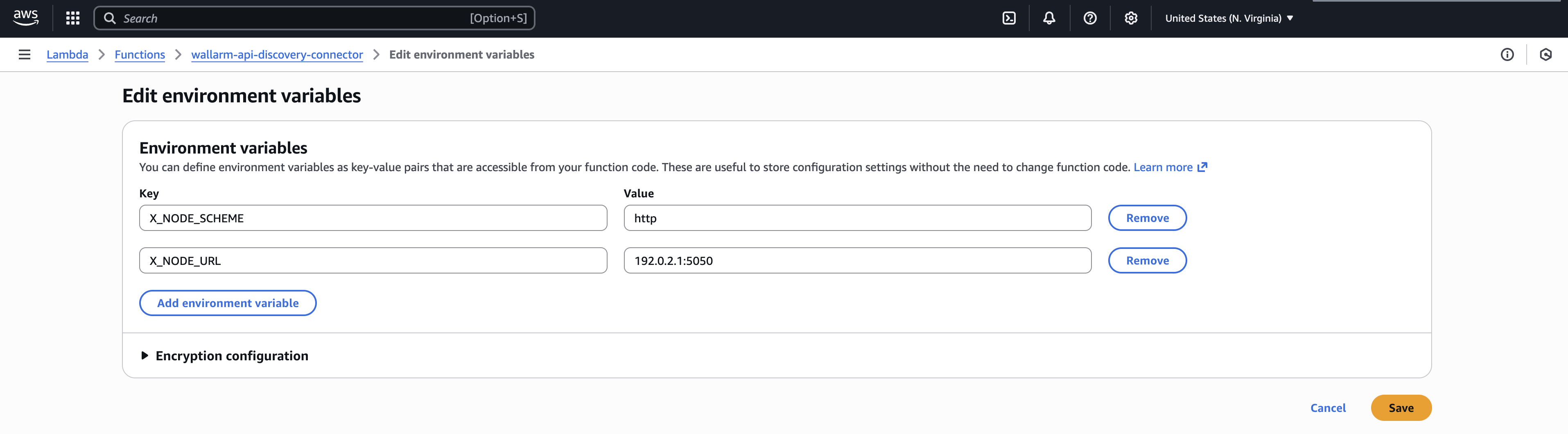
Go to the Configuration tab → Environment variables → Edit.
-
Click Add environment variable and specify the following environment variables for Node communication:
-
X_NODE_URL- Native Node DNS name or IP address, including a port if necessary (e.g.,node.example.comor192.0.2.1).Port requirement
X_NODE_URLmust include the port that the Native Node is listening on. For example, if the Native Node is deployed inconnector-servermode withconnector.addressset to:5050,X_NODE_URLmust include the port5050(e.g.,192.0.2.1:5050). -
X_NODE_SCHEME- Native Node protocol (httporhttps), depending on how the Node was deployed and whether TLS is enabled.
-
-
Click Save.
-
Go to the Configuration tab → General configuration → Edit.
-
Under "Timeout", set a value sufficient for processing a batch of logs (e.g., 30 seconds to 1 minute).
-
Click Save.
You have now configured the Lambda function so it can receive log events and forward metadata to the Wallarm node.
5. Configure CloudWatch API logging using the API Gateway console¶
-
In the main navigation panel, choose APIs, then click the name of your API.
-
Go to Stages → your stage (e.g.,
prod), scroll down to the Logs and tracing section, and then click Edit. -
Under CloudWatch logs, select Errors and info logs and toggle on Custom access logging.
-
Under Access log destination ARN, specify the ARN of the CloudWatch log group where logs will be written.
If the group does not exist, create it and copy the ARN. The ARN has the following format:
arn:aws:logs:region:account-id:log-group:group-name. -
In the Log format section, paste the following JSON log format (optimized to include only essential fields):
{ "requestId": "$context.requestId", "httpMethod": "$context.httpMethod", "path": "$context.path", "protocol": "$context.protocol", "status": "$context.status", "responseLength": "$context.responseLength", "requestTime": "$context.requestTime", "requestTimeEpoch": "$context.requestTimeEpoch", "responseLatency": "$context.responseLatency", "integrationLatency": "$context.integrationLatency", "integrationStatus": "$context.integrationStatus", "errorMessage": "$context.error.message", "stage": "$context.stage", "domainName": "$context.domainName", "sourceIp": "$context.identity.sourceIp", "userAgent": "$context.identity.userAgent" } -
Click Save.
You have configured CloudWatch API logging in API Gateway. The Lambda function is now able to process logs once the subscription filter is active.
6. Connect CloudWatch Logs to Lambda (subscription filter)¶
-
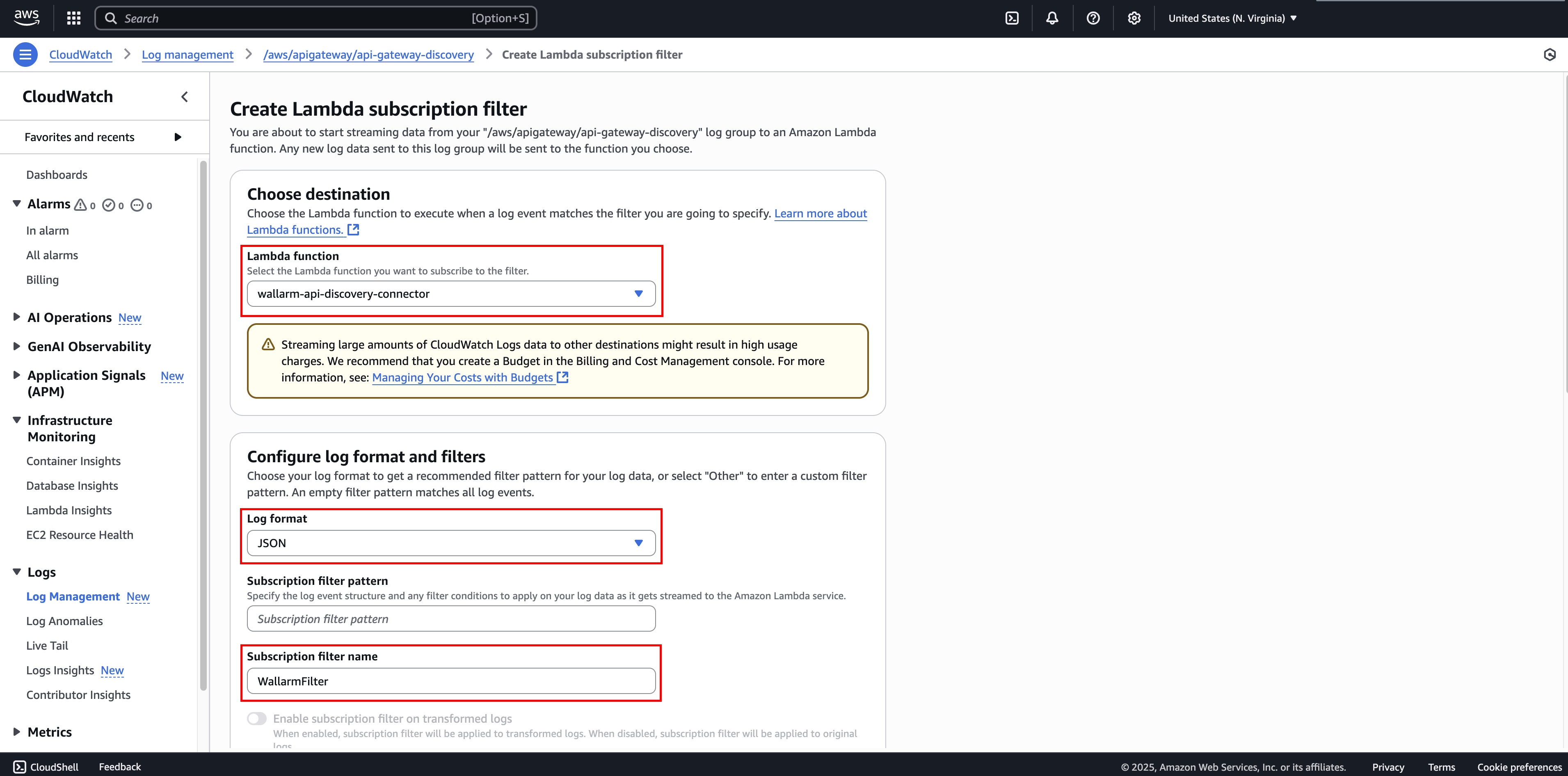
Go to CloudWatch Console → Logs → Log groups.
-
Find and select the log group you have specified in the API Gateway console in Step 3.
-
Click Actions → Subscription filters → Create Lambda subscription filter.
-
Select the Lambda function you have created in Step 3 (e.g.,
wallarm-api-discovery-connector). -
Under "Log format", select JSON.
-
You can leave "Subscription filter pattern" empty or configure filtering if necessary.
-
Under "Subscription filter name", specify a filter name (e.g.,
WallarmFilter). -
Click Start streaming.
By completing this step, you have linked the API Gateway log group to the Lambda function. The function will now start receiving and processing log events.
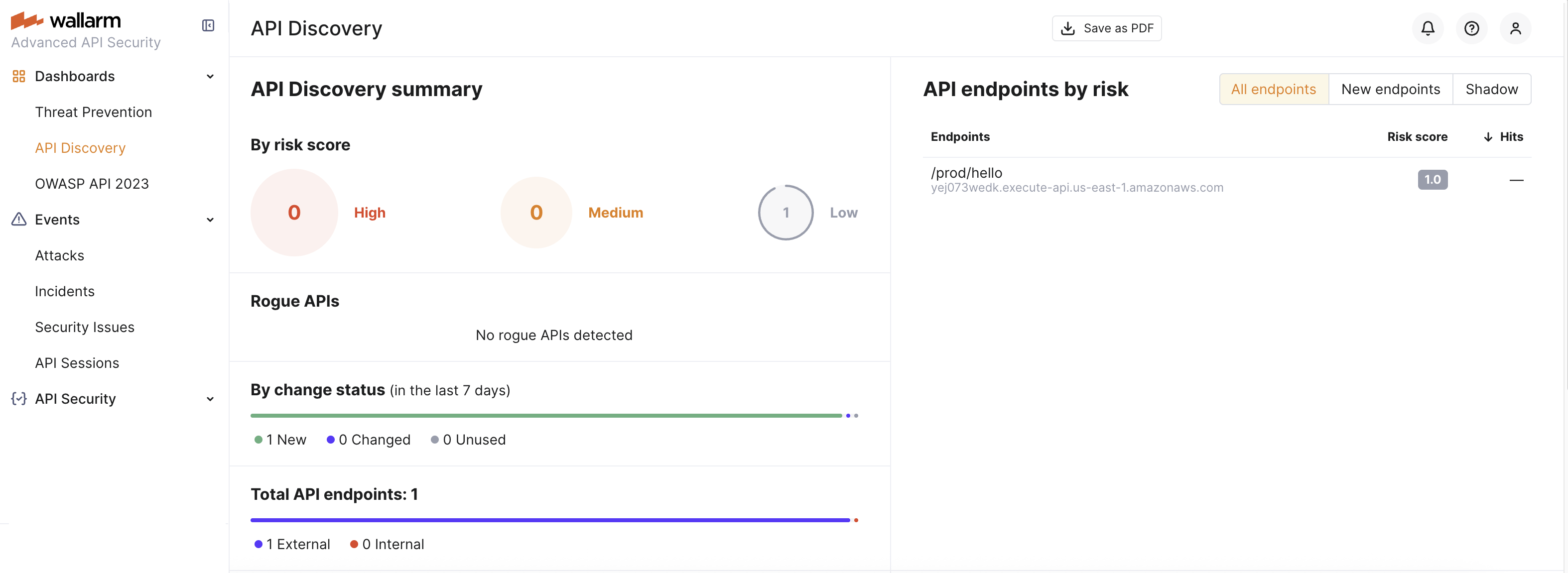
7. Check the API Discovery inventory¶
If the AWS infrastructure was deployed correctly, the API Discovery feature is automatically enabled.
Generate traffic to your API endpoints (e.g., using curl) to build the API inventory and populate the API Discovery dashboard.
Wallarm builds the API inventory only after receiving a sufficient number of requests for each endpoint.
If you have any issues, refer to the "Logs and troubleshooting" section.
Logs and troubleshooting¶
If API Discovery is not working:
-
Verify the environment variables in the Lambda function
For troubleshooting, you can also review the following logs:
-
Native Node logs:
/opt/wallarm/var/log/wallarm/go-node.log -
Lambda logs:
/aws/lambda/<your-lambda-function-name>(e.g.,/aws/lambda/wallarm-api-discovery-connector) -
API Gateway logs:
/aws/apigateway/<your-api-gateway-name>